 CLICK HERE TO DOWNLOAD THIS IMAGE & COLOR IT IN!
CLICK HERE TO DOWNLOAD THIS IMAGE & COLOR IT IN!Hey everyone. Rob here. As most of you know, the Gartner Security and Risk Summit wrapped last month, and it was a true level-setting exercise for the future of cybersecurity technology and frameworks in ‘25 and ‘26. Resilience is the name of the game, and organizations are embracing a stackable, “brick-by-brick” approach to ensure they lay the foundation well and ensure that nothing’s missed.
I was sent this image from an event attendee, and it really got me thinking, so I had to put this together for you. I’ll put it below so you can see for yourself:
In essence, it proves what IR consultants and cybersecurity professionals have known all along: when the dragons come, all your detection and protection tool investments go out the window, and it’s how you respond that matters.
Cyber expert Timothee Youngblood expanded on this thought in one of his recent LinkedIn posts, reminiscing about his prior experience as CISO of Kimberly-Clark during the infamous NotPetya Malware Outbreak.
Talk about a side quest.
Overseeing 200+ global manufacturing plants, Timothee recounted how the proactive application of a Microsoft emergency patch mitigated damage, ultimately resulting in 0 infections or events for the company.
Scout, our Co-founder, Chief Design Officer, and protection paladin extraordinaire, was inspired by his post. She reached out and asked the question we’ve all been wondering:
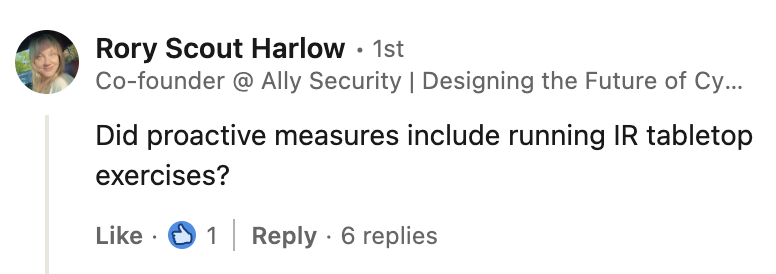
Timothee affirmed that this experience, along with countless other side quests he and his team completed, reinforced the importance of proactive security to their shareholders.
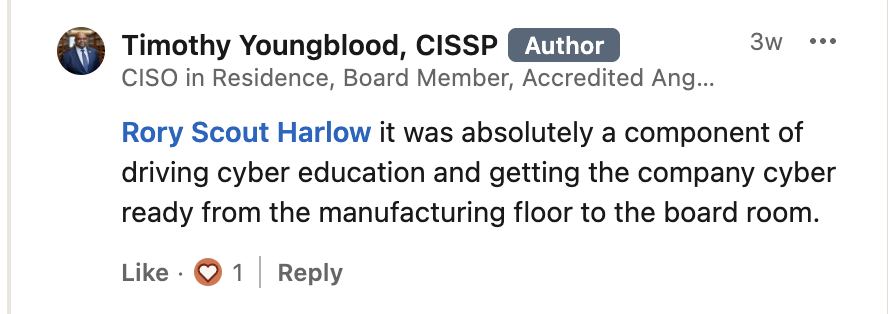
(We were a little excited about that.)
It’s not always this easy to win favor, though. Especially in the boardroom.
We need to pose two secondary questions after this revelation: Since tabletop exercises—and the involvement of IR consultants—typically happen after the damage is done, what if we could shift the narrative and make preparedness the norm?
How much could an organization benefit if we flipped current models on their heads, prioritizing readiness, response quality, and collaboration (via a TTX) first and foremost?
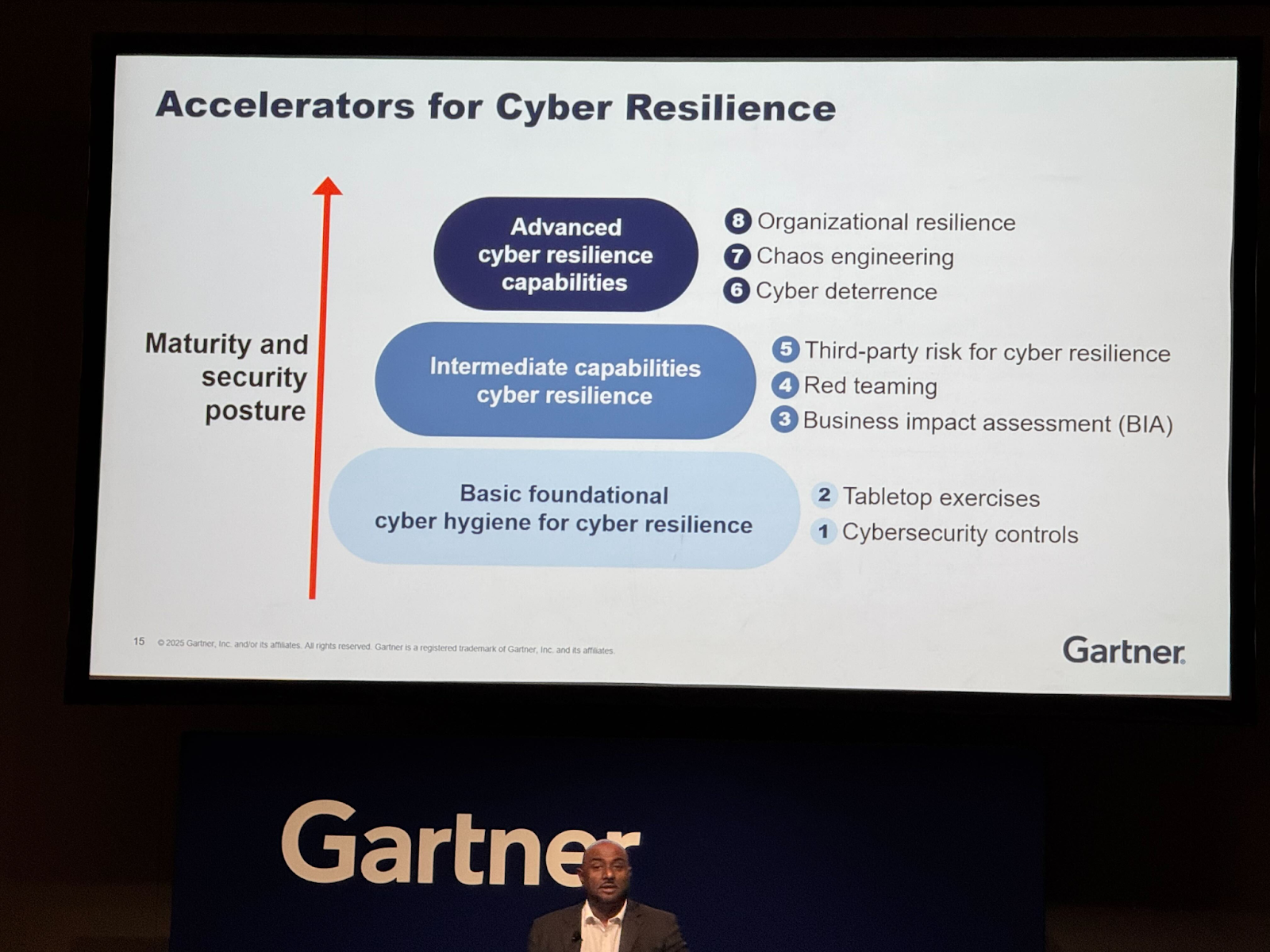
When you build your tabletop plan, look back up at Timothy’s resilience stack above. Tabletop exercises need to remain a foundational priority, but they can also be implemented across additional layers of the stack. For example, take your red team findings and develop a tabletop to communicate the importance of the findings to your executives.
Read on to learn more—and to understand how to position TTX in a way that helps you win stakeholder buy-in.
The shift that CISOs and IR consultants need to champion with their organizations goes beyond widespread, congruent protection. Why? Because threats move too fast for that, and inevitably, you’ll have a major incident.
Instead, we need to continue to pursue the organizational goal of proactive investment > reactive investing as the dragons knock at the door.
The math here should be compelling for your stakeholders, especially as situations grow dire with some of the biggest breaches to date happening in 2024 and 2025.
Coinbase, anyone?
Despite the massive cost of this breach, though, the Company’s response has been widely viewed as a massive success. They controlled the narrative, retained customer trust with complete transparency, and even got some great PR out of it by ransoming the ransomer back. That’s a win for the responders, and I can only guess they have deep-rooted, well-executed response plans in place.
The fix to this tremendous amount of risk on your organization-wide quest for organizational profitability and growth is a comprehensive tabletop plan that includes external facilitation, scenario development, and cross-functional participation.
Organizations that respond faster see ~30% lower data breach costs than those who respond slowly, according to IBM. As your tabletop exercises will come in at just a fraction of the average breach cost (which currently sits at $4.88 million), the ROI calculation becomes even clearer—and it further mandates the fundamental inclusion of a tabletop plan in your client’s resilience strategy.
Remember: Security maturity isn't measured by the number of tools you have in your stack. It's measured by outcomes.
Before you begin your tabletop program quest, start with an honest assessment of where the org is today. Do you have a comprehensive IR plan in place? Who is your Dungeon Master? Do you have an internal tabletop exercise facilitation expert to guide you? If not, those are the first tasks on the mission scroll.
Bringing in a quality 3rd party facilitator can do wonders for your tabletop plan— everyone knows there’s something at stake when a true expert is there to guide you.
I encourage anyone looking to implement a more regular tabletop cadence to start with a pro. You need to baseline what “good” looks like.
Next, it’s time to up the engagement. My tip? Scenario relevance and facilitation quality are the two most important factors in in-exercise engagement. Quality facilitators know when to push the issue, steer the conversation back to what’s important, and how to keep participants on the edge of their seats. This is not entertainment, it’s serious—but if you lose the room, you lose buy-in for your tabletop program and the improvements that come from it. As you build momentum and make wins in the C-Suite, layer complexity, departments, and new scenarios that surface as the threat landscape gets more complicated.
From here, you can kick up the cadence, but always remember to keep it fresh. Use recent breach news, internal threat intelligence findings, and recent pentest or red team results to create a gripping incident storyline. Take turns in the dungeon master’s chair—let someone else on the team run the exercise and showcase their facilitation skills. Add role play with character elements or make your participants swap roles to see things from the other perspective. And don’t forget to sprinkle in just the right amount of chaos.
Lastly, make sure the exercises don’t go to waste. Document your action items, take the steps to close the gaps, and update your plans and playbooks so you’re ready for anything.
One of the most overlooked benefits that tabletops bring is in the conversations that start at the literal tabletop. They naturally force connections and conversations that should have happened months ago, helping department heads break through barriers and facilitate communication during and after the exercise itself.
Everyone learns what the other does in a crisis—and they're able to self-identify the gaps, own their area of the response plan, and remain security-aware in their day-to-day lives.
Oh, and also: When the real emergency hits, people aren't stumbling through 3 AM conference room intros and panicking over their fifth Red Bull. They're executing seamlessly next to each other, putting the stuff they've practiced to the test.
This alone, if nothing else, shows that TTX are not just "simple, good-to-have" exercises to check off in a checklist.
They're a mandate for betterment.
They're effective.
And they're the foundational cornerstone of a strong cybersecurity posture in 2025 (and in 2035, and beyond).

Ultimately, the teams that will thrive in 2025 and beyond are the ones who venture past the best tools toward a deeper, more epic quest for cyber preparedness. These proactive paladins practice using the tools under pressure, put concepts into real-life application, and test plans frequently—and they do so because they're led by a protection paladin who works tirelessly to organize and assemble against the threat lurking just outside the firewall.
(You guessed it. The paladin is you.)
In addition to this quest, you've been given a side mission—convince the stakeholders of what you knew all along: tabletop plans and exercises are the foundation of a strong cybersecurity response. They're imperative for proactivity around cyber threats and are the key to remaining resilient when the organization is in reactive mode during an incident.
The best way to do this is to start small and show clear ROI. And there's no better way to do that than with a specially-trained Ally.
Ally supports IR consultants, CISOs, and vCISOs with Asa —your Scribe and TTX assistant—who work around the clock to help you document findings from TTX in the most digestible, compelling way for your clients in just minutes.
Picture it. No more frantically taking notes while facilitating. No more trying to remember who said what during the debrief. (Was that speaker #3 or was that the lawyer?) and no more spending your weekend writing up lessons learned. Just speed, efficiency, and ROI that help bring your stakeholders into the guild of proactive cybersecurity.
Don't miss this opportunity to strengthen your organization’s defenses. Connect today and request a demo.
About Ally Security
Ally is here to support facilitators, which in turn creates a virtuous cycle where exercises take less time, provide more value, are run more frequently, and can make every organization can be better prepared.
The unexpected wins. The client curveballs. The chaos you couldn’t have scripted if you tried. Dear Asa is your space to share the stories that don’t make it into the official post-incident report. Script, submit, and enjoy a chance to be featured or quoted in an upcoming post.
