 CLICK HERE TO DOWNLOAD THIS IMAGE & COLOR IT IN!
CLICK HERE TO DOWNLOAD THIS IMAGE & COLOR IT IN!The cyber realm is changing. Threats grow bolder, and organizations are seeking guides who can lead them through the fog of uncertainty. As a result, tabletop exercises have quickly become one of the most strategic services a security commander can offer.
Few rituals are as revealing or as transformative as gathering the party around the table to walk through a tailored scenario. In this guide, we’ll explore how to hone your TTX craft, shape it into a repeatable service line, and package it in a way that empowers both Facilitators and the clients they serve.
The journey along the path to preparedness begins long before a real cyber attack. Tabletop exercises give teams a chance to rehearse, reflect, and strengthen their response before the alarm bells sound. To understand their impact, we first need to understand the exercise itself.
A tabletop exercise, or TTX, is a guided and discussion-based simulation of how a team will respond during an unfolding cyber incident. The scenario might involve a ransomware assault, a sensitive data leak, or the discovery of an insider threat lurking in the castle’s archives.
Picture the group assembled around a map-filled war room. The Facilitator introduces the opening move of the adversary, and participants talk through how they would detect the threat, who they would notify, and which actions they would take. The party practices how to respond, tracing each clue and decision as if the adversary were already within the keep.
The purpose of a TTX is not to perform. It is to reveal. As teams discuss each step of the scenario, they discover where communication falters, where role clarity fades, and where plans rely too heavily on optimism.
Most organizations already stand behind sturdy defenses such as endpoint detection and response, email and network security, and multifactor authentication. These are the battlements and watchful guards of the digital realm. Yet, when a breach occurs, technology can only carry the fight so far. The moment the signal fires flare, it is the people inside the walls who determine how the story unfolds.
Studies like Marsh’s Cybersecurity Signals Report show a clear pattern. Organizations that invest in preparedness activities move faster, lose less, and inspire greater confidence from their stakeholders. Incident response training is the difference between a regiment that has drilled together and one meeting for the first time on the field.
In a world where reputational damage can spread faster than malware, tabletop exercises transform incident response plans from static scrolls into living, tested strategies. A practiced response consistently outperforms a theoretical one, and in the safety of the exercise chamber, teams build the muscle memory they will rely on when a real foe arrives.
The Facilitator’s role in a TTX is akin to that of dungeon master, part guide and part storyteller. He or she illuminates decision points, challenges assumptions, and helps the team follow the unfolding trail of clues. A tabletop exercise is not a script to be read. It is a conversation to be guided, challenged, and brought to life.
A skilled Facilitator creates an environment where teams feel safe acknowledging gaps and asking critical questions. This is where the real magic happens. Hidden dependencies surface. Misunderstandings resolve. Leaders find clarity as they witness how decisions ripple throughout the realm. What begins as a simulation transforms into a shared moment of truth about the team’s readiness.
A map of the TTX journey should look something like this:
Scenario → Discussion → Decision Points → Action Items → Improved Response Plan
In the hands of a capable Facilitator, a TTX becomes more than a compliance task. It becomes a a spark of momentum and a clear step forward on the path to preparedness.
For MSSPs, vCISOs, and independent Facilitators, tabletop exercises are a reliable way to showcase the value of the systems, controls, and roadmaps you have forged with your clients. A single well-run TTX can uncover more about a client’s true capabilities than months of check-ins or slide decks.
The exercise becomes a shared campfire where progress is visible, priorities come into focus, and clients gain confidence in the IR roadmap. Each TTX produces fresh insights and action items, turning your managed security services into an ongoing narrative of maturity rather than a series of one-off short stories.
Most organizations understand that cyber incidents are inevitable, yet many still underestimate the impact of a digital siege. Tabletop exercises reveal how the party truly moves and responds when the quiet breaks. There are a few common levers Facilitators can pull to rally leaders toward regular and meaningful TTX practice.
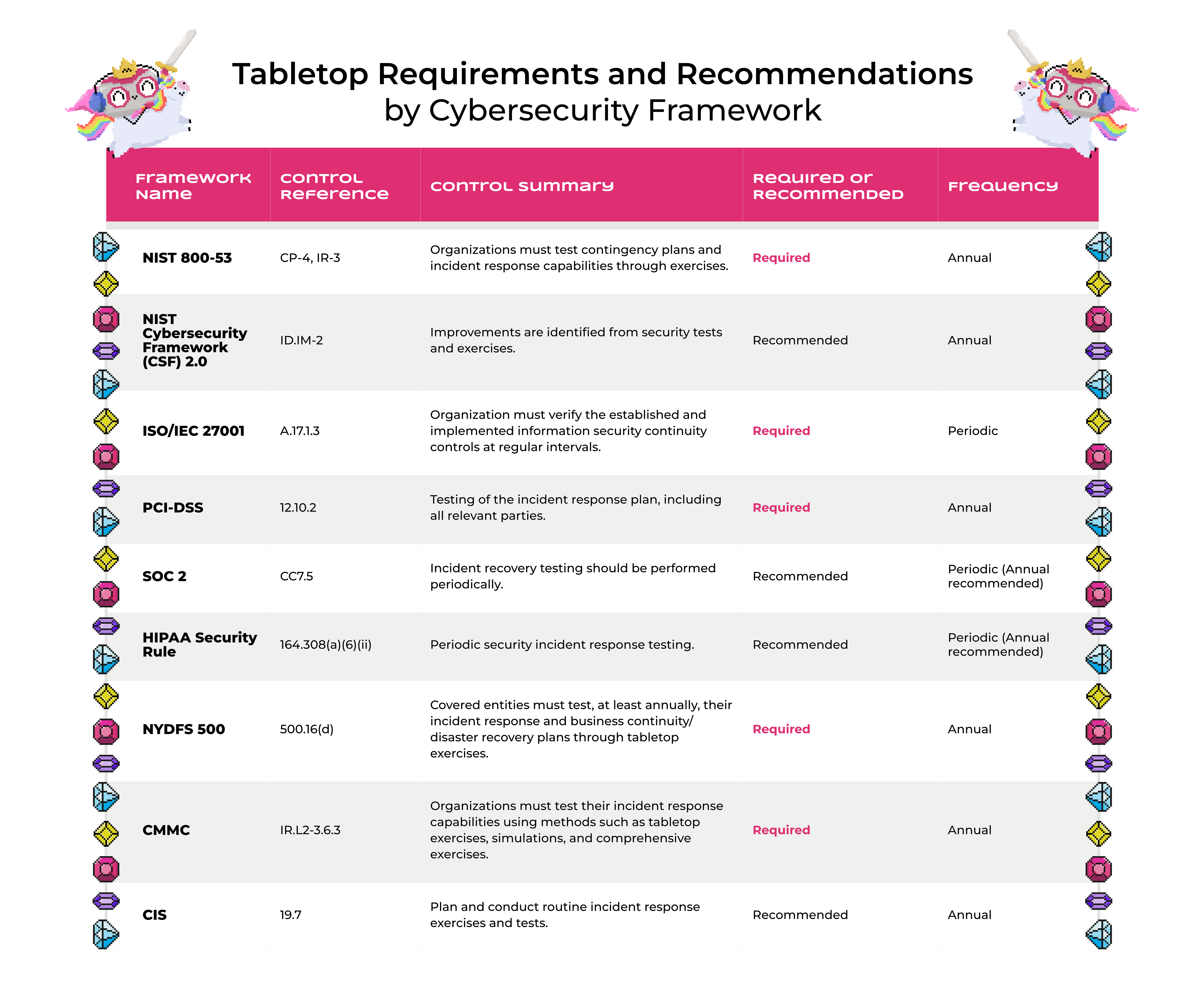
When organizations begin forming their security programs, the first questions that first echo through the hall are related to compliance. “Do I need to run tabletop exercises for CMMC? For ISO 27001? For PCI? For HIPAA?”
These questions arise because many frameworks do, in fact, require incident response testing such as tabletop exercises. The compliance driver is your opening move. It's also your opportunity to move your clients' program past the annual checkbox to a more comprehensive exercise program. Give them a good first taste, then steer them toward the path to preparedness once they’re bought in.
In the modern realm, cyber insurers are the cautious coinpurse funding the organization’s safety net. They do not simply ask whether an organization has a written response plan. They want to know whether the party has tested it, sharpened it, and can wield it well under pressure. Slow or chaotic response leads to costly claims, and insurers have grown wise to the gap between a polished policy and an unpracticed team.
A well-documented TTX program serves as the proof that cyber insurers seek. It shows that the organization can detect trouble quickly, coordinate defenders, and recover before the inferno spreads. It also demonstrates that the party can follow the insurer’s expected playbook, which typically involves notifying the carrier quickly, coordinating with empaneled IR vendors, and aligning decisions with policy requirements when the arrows start flying. For many clients, this preparation can reduce cyber insurance premiums and strengthen insurability, providing a measurable ROI.
Auditors, both internal and external, take a similar approach. They look for signs of operational maturity, not just an anthology of written procedures. Tabletop exercises provide living proof that the organization can follow its own playbook during times of crisis. They prevent unpleasant surprises during assessments and demonstrate operational validation, not just policy existence.
For Facilitators, this is another place where you become the trusted guide. You help clients gather the proof, show their preparedness, and face insurers and auditors as seasoned parties ready for the trials ahead.
For many leadership teams, a single well-run tabletop exercise becomes the moment the veil lifts. What once lived as a tidy IR PDF in the archives suddenly takes shape as a living, breathing test of the kingdom’s resilience. It is often during that first exercise that a board member or executive quietly realizes, “Our response plan is not something to read. It is something we must practice.”
Tabletop exercises give leaders something they seldom get to experience: true situational awareness. They begin to see:
This shift in awareness often unlocks funding, staffing, and tooling. Once leaders grasp the consequences of inaction, the obstacles that slow security programs begin to dissipate. A shared understanding takes shape, and with it, alignment on what truly matters.
Tabletop exercises also serve as a powerful convening ritual. They gather the right people (technical leaders, business owners, communicators, and decision-makers) around a focused narrative. When the entire party sees the same risks and the same moments of hesitation, priorities snap into focus.
To help summarize these ideas, picture the following:
A well-run tabletop does not merely test readiness. It awakens it.
Once organizations understand and meet their compliance obligations, many assume they have reached the end game. Their ledgers are updated, their policies stamped, their auditors satisfied. Yet, in the world of cybersecurity, compliance is only the threshold of the adventure. It certifies that defenses meet minimum standards, but it cannot guarantee victory when a real combatant emerges.
Compliance requirements create a baseline of expected controls, but the tactics used by digital bandits evolve faster than regulations can be drafted. When a client says, “We’re compliant, so we’re safe,” it’s like believing the party is ready to face the final boss after clearing only the tutorial mission.
Compliance might get the guards posted, but it will not teach them how to respond when the enemy swaps strategies mid-attack or when two crises strike at once. Only practice builds that instinct.
This is where tabletop exercises shine. They show whether the party can execute a plan from the war room, not merely recite it around a calm council table. A TTX places teams inside the tension of a crisis, where uncertainty thickens the air and every choice feels like it carries weight, but without the smoke and ruin of a real breach.

As these exercises become routine, organizations shift from asking “Do we have a plan?” to “Can our people follow it when the enemy is at the gate?” That shift marks the true divide between a party that freezes at the first clash and a party that moves with practiced instinct.
Even the most meticulously inked policies cannot replace a party that knows how to move as one. A single tabletop exercise often sparks an “aha moment” where teams finally see how intertwined their roles truly are when the alarm bells sound. What seemed like isolated responsibilities on paper suddenly reveal themselves as shared quests in a single, high-stakes campaign.
Executives begin to understand how their orders steer containment efforts. Technical paladins see how their actions shape legal, HR, and PR responses. Communicators realize the importance of timing, tone, and coordination. The entire cast becomes aware of how easily the party can crumble when one role hesitates or misunderstands its part.
This is when tabletop exercises become a cultural catalyst, the final ingredient in the alchemical process that generates incident response preparedness. The kingdom grows more resilient not because the documentation improves, but because synergies are unlocked as people begin to trust each other’s movements in the dark.
Designing a powerful TTX program is less about producing a single grand spectacle and more about rehearsing a rhythm of practice, reflection, and improvement. A Facilitator who helps clients build this rhythm becomes more than a guide. He or she becomes the architect of the kingdom’s ongoing preparedness. The following steps offer a practical path for shaping an epic exercise program.
Every kingdom has something it guards above all else: the systems, data, and processes that keep the realm alive. Before crafting any scenario, a Facilitator must help the client identify these crown jewels. Are they safeguarding intellectual property? Patient data? Payment systems? Operational technology?

Once these treasures are named, they become the compass that guides every scenario you craft. Instead of relying on generic “ransomware 101” drills, you forge exercises that strike at the heart of what the kingdom values most. The room leans in. The stakes sharpen. And the party understands why preparation is not optional.
Rather than lump everything into a massive annual tabletop, divide the effort into three or four focused exercises throughout the year, each tailored to a different faction:
Different parties gather for these quests, each approaching the same looming threat from their own vantage point. The technomancers defend the server keep, the commanders order rulings from the strategy hall, the operations guild keeps the realm running, etc. This structure keeps sessions short, lively, and easy to schedule while steadily leveling up the entire organization. With every quest completed, the kingdom grows wiser, quicker, and far more battle-ready.
A tabletop exercise becomes even more effective when conducted alongside other cybersecurity rituals. Facilitators can weave the threads together:
After all, most executives never fully absorb a long pentest report. They hand it to IT or infosec and hope the risk fades quietly in the background. But bring those findings into a tabletop, and suddenly the threat becomes as tangible as the gold in the castle vault.
A tabletop exercise may end when the scenario concludes, but the true adventure begins when the After Action Report scrolls are unrolled. Every insight uncovered at the war table (every hesitation, every miscommunication, every unguarded doorway) unlocks a new side quest, where the reward is better IR preparedness.
Each exercise should yield clear, actionable tasks tied to specific roles, timelines, and outcomes. These should be specific duties assigned to named heroes: hasten this process, sharpen that communication path, clarify this decision point. When framed this way, gaps become opportunities for growth rather than brands of failure.
A seasoned Facilitator helps the kingdom keep a running quest log, tracking what has been completed and what remains on the board. Over time, this chronicle becomes far more than documentation. It becomes a record that proves the party is growing stronger, exercise by exercise, season by season.
By capturing progress and closing quests, you show clients not just where they stand, but how far they’ve come. And that, more than anything, keeps leaders invested in the next tabletop.
Offering tabletop exercises as a service is one of the most reliable ways Facilitators, MSSPs, and vCISOs can strengthen client relationships, demonstrate value, and build recurring revenue. Let’s explore how to design packages that scale while delivering exercises which feel both polished and personal.
Before setting prices, Facilitators must understand the effort behind each engagement. Every tabletop carries its own hidden labors: drafting the scenario scrolls, guiding the party through the session, gathering the clues unearthed, and infusing them in a polished After Action Report. Additionally, there may be council briefings with executives or follow-up coaching once the dust settles.
Tracking this work reveals the real cost of the expedition. Without it, prices become guesswork, margins wobble like an unsteady bridge, and quality drifts. When these costs are properly scribed, you can formulate packages with confidence, scale offerings with intention, and avoid becoming the overworked wizard who undercharges for every spell.
When you create tiered cybersecurity packages, you give clients multiple ways to progress, level up, and build lasting preparedness across multiple sessions. Most Facilitators find that a three-tier structure strikes the perfect balance between clarity and flexibility.
This tier is designed for organizations taking the first step on the path to preparedness, likely to fulfill a compliance requirement.
Think of this as “Session Zero” where an organization drafts its character sheets for the first time. This tier introduces the party to the world, the rules, and the value of gathering around the table to rehearse response.
After a client has braved a handful of opening encounters, the next step is to maintain momentum. Running the same ransomware tale year after year dulls the senses and puts half the table to sleep. This tier introduces variety and evolution.
In this tier, teams begin to recognize patterns, close gaps, and approach incidents with growing confidence. The campaign becomes richer, more complex, and far more rewarding.
For kingdoms committed to resilience, insurance readiness, or regular board-level reporting, this is the premium tier.
This tier transforms tabletop exercises from isolated drills into an ongoing discipline. It becomes the backbone of the client’s preparedness program.
Not every security leader is automatically a skilled Facilitator. Guiding a room, reading the players, pacing the narrative, and prompting meaningful decisions all take practice. As previously stated, a TTX Facilitator is not unlike a Dungeon Master: half storyteller, half tactician, all orchestrator of the experience.
Encourage clients (and your own team) to level up their facilitation craft by:
The right tools free the Facilitator to focus on guiding the party through the scenario instead of capturing every detail or wrestling with slide decks.
One final note, calling in external Facilitators may also prove beneficial when neutrality or specialized expertise is needed. If this need arises, drop us a line. We’ve befriended a legion of quality providers over the years!
Tabletop exercises are the training grounds where teams achieve true readiness by transforming written plans into lived experience. For cybersecurity pros, offering TTXs as one of your services is both a strategic advantage and a powerful way to help clients build resilience.
Ally strengthens this work by giving Facilitators the tools of a seasoned Dungeon Master: automated note capture so you can focus on guiding the room, standardized preparedness metrics that track improvement across quests, and rapid, consistent After Action Reports conjured for executives within minutes. With administrative burdens lifted, you gain more time to spark meaningful dialogue and produce richer, more actionable outcomes.
If you’re ready to scale your TTX-as-a-Service offerings, deliver high-value results, and guide clients along the path to preparedness, Ally is here to equip you for the adventure ahead. Book a demo and let’s chat about how we can empower your next campaign.
About Ally Security
Ally is here to support facilitators, which in turn creates a virtuous cycle where exercises take less time, provide more value, are run more frequently, and can make every organization can be better prepared.
The unexpected wins. The client curveballs. The chaos you couldn’t have scripted if you tried. Dear Asa is your space to share the stories that don’t make it into the official post-incident report. Script, submit, and enjoy a chance to be featured or quoted in an upcoming post.
